3 min read
Don’t Have a Software Bill of Materials (SBOM) Security Strategy Yet?
Well, it’s a good time to start preparing one. The Biden Administration recently released an Executive Order requiring federal agencies to obtain...
We've crafted solutions tailored to your firm
The world of insurance for law firms can be confusing, and difficult to navigate. We've created this glossary because these common insurance terms should be easy to understand.

The dark web has changed in the past few years. As increasing numbers of cybercriminals use the dark web for exposure extortion sites that publish information on recent attacks, everyone from executives to journalists are spending more time on the dark web. So, let’s dive into how it works, and explore the background, trends, and tips for keeping your organizations safe.
The Dark Web 101
We’re going to start with a warning. The dark web is not safe. Just browsing to a site can infect your device with some pretty nasty malware, so proceed with caution or better yet, don’t browse the dark web at all. When security researchers browse, we do so from sandboxed computers to protect our network. Now, on to the basics.
The dark web is popular with criminals because it provides anonymity. It is built on top of the regular internet, uses different browsers (the most popular is Tor), and requires custom protocols and software to access sites using various security protocols. On a normal website, your traffic goes to a web server. On the dark web, you go through multiple intermediary computers (frequently 3-5) before reaching your destination. By using security protocols while making these connections, it makes it impossible for others to track your actions.
The most popular protocol, onion routing, ensures anonymity because the source and destination cannot be seen, and messages are encrypted in layers (like an onion). Each node peels off the outer layer and exposes the next address of the next destination. It encrypts the routing data to ensure no one can see your entire path—this is what provides anonymity. We won’t go into encryption here, but you can learn more in these videos: How Encryption Works and How the Dark Web Works.
How do you reach a site on the dark web using the Tor browser? You travel a “circuit,” which is a path through the network that consists of a:
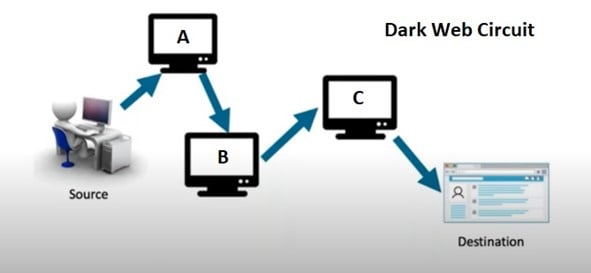
The image above shows you an example of a dark web circuit and how it goes through multiple computers to get to the destination.
If you’re browsing, you can’t tell who is running the site you’re visiting and vice versa. As we mentioned, anonymity is the foundation of why most people use the dark web. This way, the FBI cannot map your computer to the website you are visiting—a clear benefit for cybercriminals.
Does this mean the dark web is private? NO. Onion routing software is designed to preserve anonymity, not confidentiality. While you can add additional encryption software such as TLS and PGP, it’s not always included by default. If the content is not encrypted, any information you enter, or specific hardware fingerprints could be captured if a node is compromised and someone is watching. Most famously, Julian Assange founded WikiLeaks by sourcing massive streams of information that he gathered by monitoring traffic on a dark web exit node.
How Do You Get to the Dark web?
Many Virtual Private Networks (VPNs), Reddit, and Reddit’s evil cousin Dread (which is more of a criminal forum), all have listings of popular sites on the dark web. If you use Tor to access the dark web, many of the addresses will look very different and end in “.onion”.
What Can You See on the Dark Web?
You can visit “normal” websites (also called “clear web” sites) like Google.com, but it may run slower with each different computer you are routed through, and pages may be in a different language since you can’t predict the countries through which your traffic will travel. One of the key differences between the dark web and how the normal a.k.a. clear web works, is that the dark web is more difficult to navigate. To find sites on the dark web, many people use a site that serves as a directory or “search engine,” such as the Hidden Wiki. There are also other “search engines” like Haystack, Torch, and Recon, but these sites are all incomplete since it is not possible to “crawl” every site on the dark web, and addresses change often (as frequently as every few days or hours). So, while these guide sites are essential to finding your destination, you should be very cautious.
What are some of the popular destinations?
An Inside Peek at Dark Web Marketplaces
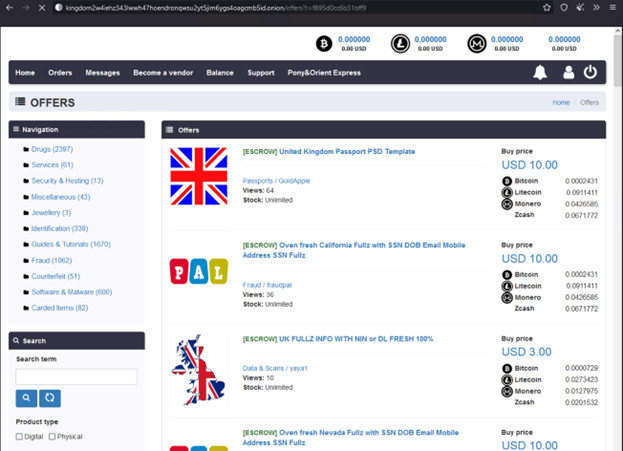
All this information is well and good, but we bet you’d like to take a peek at the dark web. So, let’s dive right in! Our first stop is the Kingdom marketplace. Below is a screenshot of fresh full data profiles and UK passport templates with prices ranging from $3 – $10.
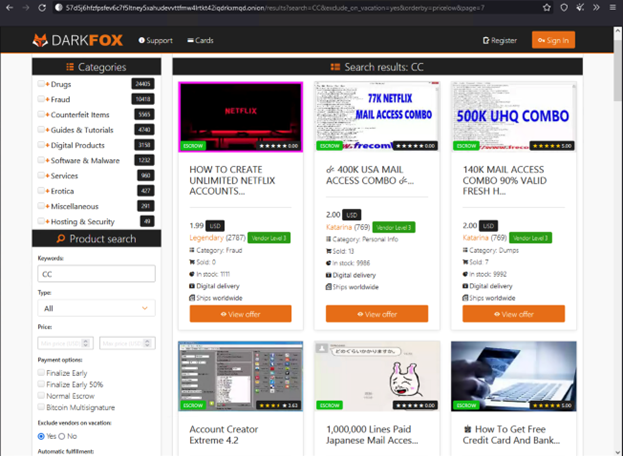
Our next stop is the DarkFox marketplace with images of email addresses, account creation tools, and hacking advice for sale.
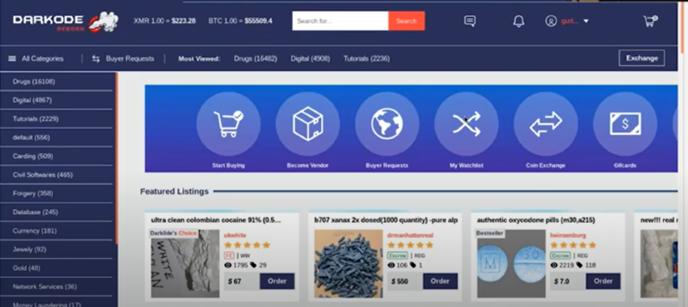
Our final stop is the DarkOde marketplace. In this screenshot you see listings for drugs rather than stolen information. You may notice that all three of these sites look quite similar to a regular clear web e-commerce site, just with illegal products. There are advanced search features, notifications, and customer service buttons, which make it easy for the criminal community to shop the markets.
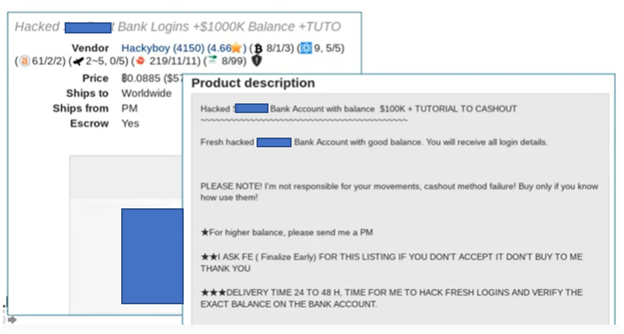
To provide visibility into the listings themselves, we have an example of the additional information you can find once you click on a listing. In the next image below, you can see an ad on another site selling bulk bank logins. These sample images don’t capture the full range of products available in dark web marketplaces. Criminals also sell hacking tools, access information, and even offer their services—complete with their hacking resume. Watch this video on exposure extortion or read The 4 Top Cybersecurity Threats of 2022 to see more dark web extortion sites.
Digging Into the Dark Web Trends
Let’s look at what is new and exciting on the dark web.
How Can you Keep Your Information Off the Dark Web?
The key is to prevent your information from being stolen in the first place. Most of the time you can’t control data disclosures because organizations that have your information get hacked. However, there are three basic cybersecurity strategies you can use to reduce the risk of hackers acquiring and effectively using your information:
We hope you now have a better understanding of the dark web, what to watch out for, and how to protect your organization. For all the ways that the dark web has matured and may look more like the clear web, the dark web is still like the wild west of old—criminals can be anywhere and the rule of law has a very limited reach. If you decide to visit the dark web, do so carefully.
This blog is distributed with the permission of LMG Security.
At LMG, our singular focus is on providing outstanding cybersecurity consulting, technical testing, training, and incident response services. Our team of recognized cybersecurity experts have been covered on the Today Show and NBC News, as well as quoted in the New York Times, Wall Street Journal, and many other publications. In addition to online cybersecurity training, LMG Security provides world-class cybersecurity services to a diverse client base located around the United States and internationally.

3 min read
Well, it’s a good time to start preparing one. The Biden Administration recently released an Executive Order requiring federal agencies to obtain...

4 min read
This blog post is in partnership with LMG Security. With professional hackers and cybersecurity criminals posing a constant threat to law firms...

4 min read
As we begin a new year, it’s time to reflect on the strengths and weaknesses of our cybersecurity posture. Now more than ever, it’s important to...